Wireshark使用技巧之三: 利用text2pcap转换Hex文本到pcap
做为工程师,平时会抓一些数据包进行分析包的结构,但是有些时候抓的信息是dump文件,没有经过编译的,所以无法读取,例如在65/76上用Netdr抓下来的出方向的数据包,仅仅能看到Layer2的信息,Layer3的信息却看不出来。有些时候,我们需要这些信息,所以要想根据这些Layer3的 Payload,推断出3层信息。这时就涉及到编译的过程,如何把十六进制的信息转换成可读的数据?转换方法有很多种,在此我将用“text2pcap”这个小 工具来完成这个任务。
------- dump of outgoing inband packet -------
interface Gi3/0/1, routine cwan_fastsend, timestamp 00:00:41
dbus info: src_vlan 0x3FD(1021), src_indx 0x380(896), len 0x50(80)
bpdu 0, index_dir 1, flood 0, dont_lrn 1, dest_indx 0xBF(191)
06028018 03FD7800 03800000 50000000 00000000 00000000 00000000 00BF0000
mistral hdr: req_token 0x0(0), src_index 0x380(896), rx_offset 0x30(48)
requeue 0, obl_pkt 0, vlan 0x0(0)
destmac 01.00.5E.00.00.02, srcmac 00.1B.0D.E6.F0.C0, protocol 0800
layer 3 data: 45C0003E 00000000 01115469 42424242 E0000002 02860286
002A84B4 0001001E 02020202 00000100 00140000 00000400
0004000F 00000401 000003FD 00000141 00000000 080C
对于text2pcap工具,他是wireshark自带的一个小工具。就在wireshark的根目录下,通过DOS来运行。关于此工具的具体内容,请看帮助文档,在帮助文档里举得例子采用的偏移量是8字节:
000000 00 e0 1e a7 05 6f 00 10 ........
000008 5a a0 b9 12 08 00 46 00 ........
000010 03 68 00 00 00 00 0a 2e ........
000018 ee 33 0f 19 08 7f 0f 19 ........
000020 03 80 94 04 00 00 10 01 ........
000028 16 a2 0a 00 03 50 00 0c ........
000030 01 01 0f 19 03 80 11 01 ........
另外我们可以简单的从wireshark里看到这些信息怎么编写,如图标红处,注意这里面用到的偏移量是16字节,也就是1行16 byte。
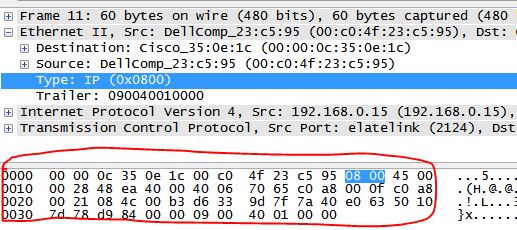
这时把Netdr的Layer3内容传化成如下格式(根据颜色的顺序,分别代表目的MAC,源MAC,协议号),并保存为txt,然后放入wireshark根目录下。
0000 01 00 5E 00 00 02 00 1B 0D E6 F0 C0 08 00 45 C0 0010 00 3E 00 00 00 00 01 11 54 69 42 42 42 42 E0 00 0020 00 02 02 86 02 86 00 2A 84 B4 00 01 00 1E 02 02 0030 02 02 00 00 01 00 00 14 00 00 00 00 04 00 00 04 0040 00 0F 00 00 04 01 00 00 03 FD 00 00 01 41 00 00 0050 00 00 08 0C
用text2pcap转换,如下所示:
C:\Program Files\Wireshark>text2pcap test1.txt test.pcap Input from: test1.txt Output to: test.pcap Wrote packet of 83 bytes at 0 Read 1 potential packet, wrote 1 packet
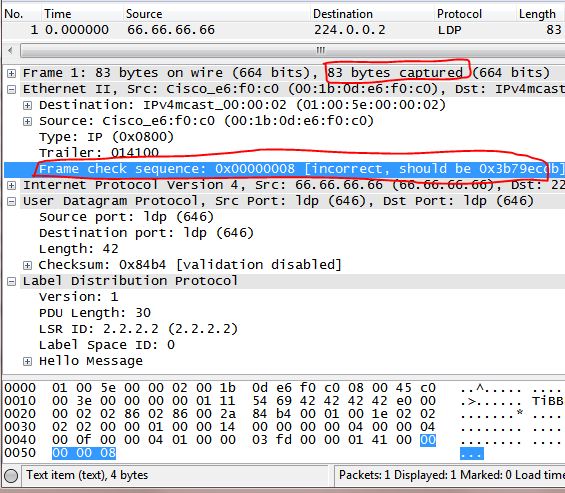
用wireshark打开这个test.pcap文件,如下图所示,不过奇怪的是,跟用Netdr的信息比,多出3字节,可能问题出在尾帧上。不管怎么样,通过这种方法,已经完全可以看出这些是什么包了。
本文出自 Frank's Blog2012-8-21 更新
如果用text2pcap解析几个包还可以,但是如果大量的包就比较麻烦了,还得把dump出来的信息一个字节一个字节排列,才能正常转换,今天同事用了另一种方法,感觉非常方便,特再此更新(注意,下面的信息已经被改动,仅仅是例子,如想尝试请拿具体的信息去decord):frank@frank% more ram.txt 00000000: FECE2122 23242526 2728292A 2B2C2D2E 00000000: 2F303132 33343536 3738393A 3B3C3D3E 00000000: 3F404142 43444546 4748494A 4B4C4D4E 00000000: 4F505152 00000000 frank@frank% hex2pcap ram.txt Frame 1 (66 bytes on wire, 66 bytes captured) Arrival Time: Dec 31, 1969 16:00:00.000000000 [Time delta from previous captured frame: 0.000000000 seconds] [Time delta from previous displayed frame: 0.000000000 seconds] [Time since reference or first frame: 0.000000000 seconds] Frame Number: 1 Frame Length: 66 bytes Capture Length: 66 bytes [Frame is marked: False] [Protocols in frame: raw:ip:data] Raw packet data No link information available Internet Protocol, Src: Dst: Version: 4 Header length: 20 bytes Differentiated Services Field: 0x00 (DSCP 0x00: Default; ECN: 0x00) 0000 00.. = Differentiated Services Codepoint: Default (0x00) .... ..0. = ECN-Capable Transport (ECT): 0 .... ...0 = ECN-CE: 0 Total Length: 74 Identification: 0xc60f (50703) Flags: 0x00 0.. = Reserved bit: Not Set .0. = Don't fragment: Not Set ..0 = More fragments: Not Set Fragment offset: 2960 Time to live: 112 Protocol: ICMP (0x01) Header checksum: 0x8dbf [correct] [Good: True] [Bad : False] Source: Destination: Data (46 bytes) [Length: 46]
版权声明:
本文链接:Wireshark使用技巧之三: 利用text2pcap转换Hex文本到pcap
版权声明:本文为原创文章,仅代表个人观点,版权归 Frank Zhao 所有,转载时请注明本文出处及文章链接
[…] https://www.wireshark.org/docs/wsug_html_chunked/AppToolstext2pcap.html http://www.zhaocs.info/wireshark-text2pcap.html http://tw.perlmaven.com/filtering-values-with-perl-grep […]
whoah this blog is magnificent i really like reading your posts.
Keep up the good work! You realize, many people are searching round for this
information, you can help them greatly.