L2TP – LAC客户端测试分析
Topology
PC—-ISP—-[f0/0]LNS[ server]
本篇仅关注测试,LAC客户端的更多内容,可以看上一篇简述《L2TP两种部署方法简述》
“Ignoring SCCRQ, tunnel from “frank” requires security, however the SCCRQ was received unprotected”去掉Ipsec配置后,PC能正常拨入并获得地址,配置跟LAC独立客户端里的LNS差不多。另外在PC上既然已经通过注册表关闭了Ipsec,那么在PC的L2TP拨号的属性配置中,关于Ipsec的相关认证就没有用了,可以忽略掉。如果不修改注册表,那么PC用L2TP拨号时会先协商Ipsec,Ipsec tunnel建立后,再协商L2TP。本文主要测试当PC不修改注册表,也就是开启L2TP/Ipsec时的L2TP拨号过程。我的测试系统是Windows8,其他系统是否默认开启L2TP/Ipsec,请自行确认。另外思科设备跟windows启动L2TP/Ipsec时,仅支持透明模式通道。下面是最初配置,后面跟着TS过程及最终配置,希望能帮助其他人解决问题。
LNS最初配置
hostname R2LNS ! aaa new-model aaa authentication ppp default local ! vpdn enable ! vpdn-group 1 accept-dialin protocol l2tp virtual-template 1 terminate-from hostname frank !---用PC的名称来选择Tunnel,在accept-dialin中没有用domain的配置 local name R2LNS lcp renegotiation on-mismatch l2tp security crypto-profile CCIE no l2tp tunnel authentication !---PC只有用户名和密码,因此Tunnel认证在这种情况下就不用了 ! username [email protected] password 0 111111 username test password 0 test ! crypto isakmp policy 10 encr 3des hash md5 authentication pre-share crypto isakmp key 123 address 12.1.1.1 ! crypto ipsec transform-set CCNP esp-3des esp-md5-hmac mode transport ! crypto map vpn 10 ipsec-isakmp profile CCIE set transform-set CCNP ! interface Loopback0 ip address 2.2.2.2 255.255.255.255 ! interface FastEthernet0/0 ip address 12.1.1.2 255.255.255.0 duplex half crypto map vpn ! interface Virtual-Template1 ip unnumbered Loopback0 peer default ip address pool l2tp ppp authentication ms-chap-v2 ! ip local pool l2tp 33.33.33.1 33.33.33.254 ip route 0.0.0.0 0.0.0.0 12.1.1.1
1. 在PC端建立L2TP拨号,目的地址为2.2.2.2发现如下报错:
*Oct 11 11:35:10.831: ISAKMP:(0):Checking ISAKMP transform 5 against priority 10 policy *Oct 11 11:35:10.831: ISAKMP: encryption 3DES-CBC *Oct 11 11:35:10.831: ISAKMP: hash SHA *Oct 11 11:35:10.831: ISAKMP: default group 2 *Oct 11 11:35:10.831: ISAKMP: auth pre-share *Oct 11 11:35:10.831: ISAKMP: life type in seconds *Oct 11 11:35:10.831: ISAKMP: life duration (VPI) of 0x0 0x0 0x70 0x80 *Oct 11 11:35:10.831: ISAKMP:(0):Hash algorithm offered does not match policy! *Oct 11 11:35:10.831: ISAKMP:(0):atts are not acceptable. Next payload is 0 ...... *Oct 11 11:35:10.839: ISAKMP:(0):deleting SA reason "Phase1 SA policy proposal not accepted" state (R) MM_NO_STATE (peer 12.1.1.1)
2. 根据debug信息,PC携带的Phase1加密属性中没有支持“hash md5”的,仅接受SHA hash,把hash改成SHA, 发现下面报错:
*Oct 11 11:53:09.855: ISAKMP:(0):Checking ISAKMP transform 5 against priority 10 policy
*Oct 11 11:53:09.855: ISAKMP: encryption 3DES-CBC
*Oct 11 11:53:09.855: ISAKMP: hash SHA
*Oct 11 11:53:09.855: ISAKMP: default group 2*Oct 11 11:53:09.855: ISAKMP: auth pre-share
*Oct 11 11:53:09.855: ISAKMP: life type in seconds
*Oct 11 11:53:09.855: ISAKMP: life duration (VPI) of 0x0 0x0 0x70 0x80
*Oct 11 11:53:09.855: ISAKMP:(0):Diffie-Hellman group offered does not match policy!
*Oct 11 11:53:09.855: ISAKMP:(0):atts are not acceptable. Next payload is 0
......
*Oct 11 11:53:09.859: ISAKMP:(0):deleting SA reason "Phase1 SA policy proposal not accepted" state (R) MM_NO_STATE (peer 12.1.1.1)
3. 查找后,Ipsec下的group跟PC的不匹配会导致这个报错,根据PC抓包发现,PC的“exchange type”是“identity protection(main mode)”,而路由器发出的isakmp “exchange type” 是 “information”。思科默认应该是group 5,修改成group 2后,发现match了:
*Oct 11 12:00:06.443: ISAKMP:(0):Checking ISAKMP transform 5 against priority 10 policy
*Oct 11 12:00:06.443: ISAKMP: encryption 3DES-CBC
*Oct 11 12:00:06.443: ISAKMP: hash SHA
*Oct 11 12:00:06.443: ISAKMP: default group 2
*Oct 11 12:00:06.443: ISAKMP: auth pre-share
*Oct 11 12:00:06.443: ISAKMP: life type in seconds
*Oct 11 12:00:06.443: ISAKMP: life duration (VPI) of 0x0 0x0 0x70 0x80
*Oct 11 12:00:06.443: ISAKMP:(0):atts are acceptable. Next payload is 0
4. isakmp的group问题解决后,又发现“invalid local address”:
*Oct 12 08:35:42.099: ISAKMP:(1001):atts are acceptable.
*Oct 12 08:35:42.099: IPSEC(validate_proposal_request): proposal part #1
*Oct 12 08:35:42.099: IPSEC(validate_proposal_request): proposal part #1,
(key eng. msg.) INBOUND local= 2.2.2.2, remote= 12.1.1.1,
local_proxy= 2.2.2.2/255.255.255.255/17/1701 (type=1),
remote_proxy= 12.1.1.1/255.255.255.255/17/1701 (type=1),
protocol= AH, transform= NONE (Transport),
lifedur= 0s and 0kb,
spi= 0x0(0), conn_id= 0, keysize= 0, flags= 0x0
*Oct 12 08:35:42.099: IPSEC(ipsec_process_proposal): invalid local address 2.2.2.2
*Oct 12 08:35:42.099: ISAKMP:(1001): IPSec policy invalidated proposal with error 8
*Oct 12 08:35:42.099: ISAKMP:(1001): phase 2 SA policy not acceptable! (local 2.2.2.2 remote 12.1.1.1)
5. 经同事提醒,问题可能出在环回地址上,crypto配置在f0/0上,但PC拨的是环回口,因此可能需要配置:crypto map vpn local-address Loopback0
配置完后再拨号,“invalid local address”没有了,又出下面报错:
*Oct 12 09:45:01.079: ISAKMP:(1005):Checking IPSec proposal 5
*Oct 12 09:45:01.079: ISAKMP: transform 1, AH_SHA
*Oct 12 09:45:01.079: ISAKMP: attributes in transform:
*Oct 12 09:45:01.079: ISAKMP: encaps is 2 (Transport)
*Oct 12 09:45:01.079: ISAKMP: authenticator is HMAC-SHA
*Oct 12 09:45:01.079: ISAKMP: SA life type in seconds
*Oct 12 09:45:01.079: ISAKMP: SA life duration (VPI) of 0x0 0x0 0xE 0x10
*Oct 12 09:45:01.079: ISAKMP: SA life type in kilobytes
*Oct 12 09:45:01.079: ISAKMP: SA life duration (VPI) of 0x0 0x3 0xD0 0x90
*Oct 12 09:45:01.079: ISAKMP:(1005):atts are acceptable.
*Oct 12 09:45:01.079: IPSEC(validate_proposal_request): proposal part #1
*Oct 12 09:45:01.079: IPSEC(validate_proposal_request): proposal part #1,
(key eng. msg.) INBOUND local= 2.2.2.2, remote= 12.1.1.1,
local_proxy= 2.2.2.2/255.255.255.255/17/1701 (type=1),
remote_proxy= 12.1.1.1/255.255.255.255/17/1701 (type=1),
protocol= AH, transform= NONE (Transport),
lifedur= 0s and 0kb,
spi= 0x0(0), conn_id= 0, keysize= 0, flags= 0x0
*Oct 12 09:45:01.079: map_db_find_best did not find matching map
*Oct 12 09:45:01.079: IPSEC(ipsec_process_proposal): proxy identities not supported
*Oct 12 09:45:01.079: ISAKMP:(1005): IPSec policy invalidated proposal with error 32
*Oct 12 09:45:01.079: ISAKMP:(1005): phase 2 SA policy not acceptable! (local 2.2.2.2 remote 12.1.1.1)
6. 经过topic,发现有人把transform-set设错了,导致出现这个错误,看上面的错误,transform attributes里是HMAC-SHA,而我设置的是esp-md5-hmac,跟这个有关系么?先改了再说“crypto ipsec transform-set CCNP esp-3des esp-sha-hmac”,再次拨号,哈哈,终于通了,看到了久违的L2TP的SCCRQ了~~再去看wireshark抓到的包,所有L2TP的包都被ESP加密了。至此搞定l2tp/ipsec!
LNS最终配置
由于l2tp的配置没动,所以仅贴出最终Ipsec部分的配置
crypto isakmp policy 10
!—Phase1认证相关信息
encr 3des
!—配置完sha后不显示在配置中
authentication pre-share
group 2
!—这个配置可以跟windows系统匹配
crypto isakmp key cisco address 12.1.1.1
!—这个密码要跟PC上l2tp拨号里的那个密码一致,否则不能通过Phase1,如下图
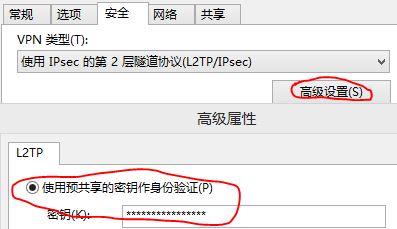
!
crypto ipsec transform-set CCNP esp-3des esp-md5-hmac
mode transport
!
crypto map vpn local-address Loopback0
crypto map vpn 10 ipsec-isakmp profile CCIE
set transform-set CCNP
PC信息
C:\Windows\system32>ipconfig /all
PPP 适配器 VPN 连接:
连接特定的 DNS 后缀 . . . . . . . :
描述. . . . . . . . . . . . . . . : VPN 连接
物理地址. . . . . . . . . . . . . :
DHCP 已启用 . . . . . . . . . . . : 否
自动配置已启用. . . . . . . . . . : 是
IPv4 地址 . . . . . . . . . . . . : 33.33.33.1(首选)
子网掩码 . . . . . . . . . . . . : 255.255.255.255
默认网关. . . . . . . . . . . . . : 0.0.0.0
TCPIP 上的 NetBIOS . . . . . . . : 已启用
以太网适配器 以太网 3:
连接特定的 DNS 后缀 . . . . . . . :
描述. . . . . . . . . . . . . . . : Microsoft KM-TEST 环回适配器
物理地址. . . . . . . . . . . . . : 02-00-4C-4F-4F-50
DHCP 已启用 . . . . . . . . . . . : 否
自动配置已启用. . . . . . . . . . : 是
IPv4 地址 . . . . . . . . . . . . : 12.1.1.1(首选)
子网掩码 . . . . . . . . . . . . : 255.255.255.0
默认网关. . . . . . . . . . . . . : 12.1.1.2
TCPIP 上的 NetBIOS . . . . . . . : 已启用
以太网适配器 以太网:
连接特定的 DNS 后缀 . . . . . . . :
描述. . . . . . . . . . . . . . . : Intel(R) 82574L 千兆网络连接
C:\Windows\system32>route print
===========================================================================
接口列表
47...........................VPN 连接
31...02 00 4c 4f 4f 50 ......Microsoft KM-TEST 环回适配器
12...00 25 90 27 5b 07 ......Intel(R) 82574L 千兆网络连接
===========================================================================
IPv4 路由表
===========================================================================
活动路由:
网络目标 网络掩码 网关 接口 跃点数
0.0.0.0 0.0.0.0 12.1.1.2 12.1.1.1 4491
0.0.0.0 0.0.0.0 192.168.1.1 192.168.1.2 4245
0.0.0.0 0.0.0.0 在链路上 33.33.33.1 11
相关信息
Implementing L2TP Voluntary/Client-Initiated Tunnel Mode Remote Access VPNs – PC跟LNS拨号,有详细的配置解释
Access VPDN Dial-in Using IPSec Over L2TP – ISP用ipsec加密,非客户端起ipsec,里面有些很好的图例
Configuring Layer 2 Tunneling Protocol (L2TP) over IPSec – LAC和LNS起ipsec加密,配置实例
Cisco Hardware and VPN Clients Supporting IPSec/PPTP/L2TP – 硬件支持信息
ISAKMP/IKE Phase 2 Connections – Phase2 失败的几种情况
你好,请问能不能把你的拓朴给出来一下啊,谢谢!
最上面不是有TOPOLOGY么?就是PC直连路由器,哪里不清楚么?