How to convert SPP into text2pcap readable format by python
Introduction
There are some internal tools that can decode SPP packets at former, but they are not work now. In some scenario, customer coudln’t do span on our asr9k, so we only need SPP, then will face to how to decode SPP result.
The article disscuss how to covert SPP original data to text2pcap readable format, then decode by text2pcap. You only do the script that can auto work. Btw, before do that, you need have python2.7 and text2pcap (integrate in wireshark). If you have python3.0 or newer, that maybe have some issue, because some function have a bit different, you need adjust them by yourself.
Solution
Original SPP data:
=~=~=~=~=~=~=~=~=~=~=~= PuTTY log 2017.12.04 17:12:19 =~=~=~=~=~=~=~=~=~=~=~= trace p stop Tracing stopped with 666 outstanding... spp-ui> trace print Packet serial 861 port4/classify: length 148 phys_int_index 0 next_ctx 0xdeadbeef time 09:10:41.407 00: 00 70 72 00 00 08 00 65 7a 00 00 00 ff ff 00 07 10: 80 30 00 00 00 00 0f 00 00 00 1f 00 00 00 00 00 20: 00 70 05 f2 42 fb 00 00 04 00 01 40 07 01 05 27 30: 06 03 0e 06 00 00 00 00 4c 00 00 00 00 00 58 00 40: 00 00 00 00 00 00 06 01 00 a1 13 41 92 60 00 b2 50: 64 41 8a 4c 08 00 45 c0 00 3e 00 00 00 00 fe 11 60: c8 25 12 ac 79 0d 34 df d0 01 02 86 02 86 00 2a 70: 75 5a 00 01 00 1e 3f da a4 0f 00 00 01 00 00 14 80: 00 00 00 00 04 00 00 04 00 5a c0 00 04 01 00 04 90: 3f da a4 0f 00 00 00 00 00 00 00 00 00 00 00 00 a0: 00 00 00 17 00 08 05 01 00 00 af c8 00 24 14 01 b0: 01 08 3f da d0 46 20 00 01 08 3f da d0 42 20 00 c0: 01 08 3f da d0 41 20 00 01 08 3f da d0 07 20 00 d0: 00 08 13 01 00 00 08 00 00 20 cf 07 00 00 07 16 e0: 4d 50 4c 53 2d 54 45 20 74 6f 20 76 61 72 30 31 f0: 2e 6b 6c 70 30 32 00 00 00 0c 0b 07 3f df 04 08 --------------------------
Python Scripts
import sys
import os
import re
import tempfile
from itertools import chain
# each packets 256 byte, fix size
lines = []
newlines = []
packets = []
if len(sys.argv) < 3 or len(sys.argv) > 4:
sys.exit(1);
# 1 = exception exit; 0 = normal exit
if len(sys.argv) > 3:
offset = sys.argv[1]
original_filename = sys.argv[2]
pcap_name = sys.argv[3]
print 'Offset: ' + offset
print 'Original SPP DATA Name: '+ original_filename
print 'New PCAP Name: ' + pcap_name
# original data:
'''
spp-ui> trace print
Packet serial 5
port4/classify:
length 148 phys_int_index 0 next_ctx 0xdeadbeef time 04:31:10.294
e0: 4d 50 4c 53 2d 54 45 20 74 6f 20 76 61 72 30 31
f0: 2e 6b 6c 70 30 32 00 00 00 0c 0b 07 3f df 04 08
--------------------------
spp-ui> trace print
Packet serial 861
port4/classify:
length 148 phys_int_index 0 next_ctx 0xdeadbeef time 09:10:41.407
e0: 4d 50 4c 53 2d 54 45 20 74 6f 20 76 61 72 30 31
f0: 2e 6b 6c 70 30 32 00 00 00 0c 0b 07 3f df 04 08
--------------------------
'''
f = open(original_filename)
for line in f.readlines():
if re.search('[0-9a-f]0: ', line):
lines.append(line.split()[1:])
f.close()
# lines data:
'''
[['4d', '50', '4c', '53', '2d', '54', '45', '20', '74', '6f', '20', '76', '61', '72', '30', '31'], ['2e', '6b', '6c', '70', '30', '32', '00', '00', '00', '0c', '0b', '07', '3f', 'df', '04', '08'], ['4d', '50', '4c', '53', '2d', '54', '45', '20', '74', '6f', '20', '76', '61', '72', '30', '31'], ['2e', '6b', '6c', '70', '30', '32', '00', '00', '00', '0c', '0b', '07', '3f', 'df', '04', '08']]
'''
newlines = list(chain(*lines))
# newlines data:
'''
['4d', '50', '4c', '53', '2d', '54', '45', '20', '74', '6f', '20', '76', '61', '72', '30', '31', '2e', '6b', '6c', '70', '30', '32', '00', '00', '00', '0c', '0b', '07', '3f', 'df', '04', '08', '4d', '50', '4c', '53', '2d', '54', '45', '20', '74', '6f', '20', '76', '61', '72', '30', '31', '2e', '6b', '6c', '70', '30', '32', '00', '00', '00', '0c', '0b', '07', '3f', 'df', '04', '08']
'''
for i in range(0,len(newlines),256):
packets.append(newlines[(i + int(offset)):i+256])
# 0 to len(), step is 256
# equal with 'print newlines[0:256]' and 'print newlines[256:512]'
# packets data
# in the example, totally 32 each packets, but not 256, only show result, not change original script
'''
[['20', '76', '61', '72', '30', '31', '2e', '6b', '6c', '70', '30', '32', '00', '00', '00', '0c', '0b', '07', '3f', 'df', '04', '08'], ['20', '76', '61', '72', '30', '31', '2e', '6b', '6c', '70', '30', '32', '00', '00', '00', '0c', '0b', '07', '3f', 'df', '04', '08']]
'''
temp = tempfile.NamedTemporaryFile()
# use temporary file to save temp data
for d1 in packets:
# d1 is a list
y=0
for z in range(0,len(d1)):
if (z + 1) % 16 == 0:
print >> temp, d1[z]
elif (z + 1) % 16 == 1:
print >> temp, "00" + str(hex(y))[-1] + "0: " + d1[z],
y = y+1
else:
print >> temp, d1[z],
print >> temp, "\n"
temp.seek(0)
# put pointer to beginnng
cmd1= 'more '+ temp.name
cmd2 = 'text2pcap ' + temp.name + ' ' + pcap_name
os.system(cmd1)
os.system(cmd2)
# finally data:
'''
0000: 20 76 61 72 30 31 2e 6b 6c 70 30 32 00 00 00 0c
0010: 0b 07 3f df 04 08
0000: 20 76 61 72 30 31 2e 6b 6c 70 30 32 00 00 00 0c
0010: 0b 07 3f df 04 08
'''
Verified
Attention: Refer to offset data, you need find L2’s mac harder, then check number, as follow example, after offset 72, L2 header begins.
xxx-M-Q4TL:Desktop xxx$ python convert-spp-text2pcap-readable.py 72 spp-test-1.txt spp-test-1.pcap Offset: 72 Original SPP DATA Name: spp-test-1.txt New PCAP Name: spp-test-1.pcap 0000: 00 a1 13 41 92 60 00 b2 64 41 8a 4c 08 00 45 c0 0010: 00 3e 00 00 00 00 fe 11 c8 25 12 ac 79 0d 34 df 0020: d0 01 02 86 02 86 00 2a 75 5a 00 01 00 1e 3f da 0030: a4 0f 00 00 01 00 00 14 00 00 00 00 04 00 00 04 0040: 00 5a c0 00 04 01 00 04 3f da a4 0f 00 00 00 00 0050: 00 00 00 00 00 00 00 00 00 00 00 17 00 08 05 01 0060: 00 00 af c8 00 24 14 01 01 08 3f da d0 46 20 00 0070: 01 08 3f da d0 42 20 00 01 08 3f da d0 41 20 00 0080: 01 08 3f da d0 07 20 00 00 08 13 01 00 00 08 00 0090: 00 20 cf 07 00 00 07 16 4d 50 4c 53 2d 54 45 20 00a0: 74 6f 20 76 61 72 30 31 2e 6b 6c 70 30 32 00 00 00b0: 00 0c 0b 07 3f df 04 08 0000: 00 a1 13 41 92 60 00 b2 64 41 8a 4c 08 00 45 c0 0010: 00 3e 00 00 00 00 fe 11 c8 25 12 ac 79 0d 34 df 0020: d0 01 02 86 02 86 00 2a 75 5a 00 01 00 1e 3f da 0030: a4 0f 00 00 01 00 00 14 00 00 00 00 04 00 00 04 0040: 00 5a c0 00 04 01 00 04 3f da a4 0f 00 00 00 00 0050: 00 00 00 00 00 00 00 00 00 00 00 00 44 7a 00 00 0060: 00 00 00 00 00 00 00 00 00 00 11 76 00 0c 0a 07 0070: 3f da d0 08 00 00 09 19 00 08 10 01 00 00 78 00 0080: 01 04 15 01 01 08 3f da d0 05 20 20 03 08 01 01 0090: 00 00 78 00 01 08 3f da d0 45 20 00 03 08 01 01 00a0: 00 00 78 00 01 08 3f da d0 06 20 20 03 08 01 01 00b0: 00 00 7e 66 01 08 3f da Input from: /var/folders/7y/8nvq5m_x1k9c7q9jbl7ysw1r0000gn/T/tmpwkQE7N Output to: spp-test-1.pcap Output format: PCAP Wrote packet of 184 bytes. Wrote packet of 184 bytes. Read 2 potential packets, wrote 2 packets (424 bytes).
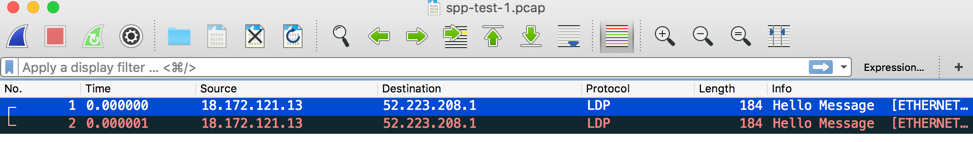
Wireshark
Detail packets, please check attachment: spp-test-1.pcap
版权声明:
本文链接:How to convert SPP into text2pcap readable format by python
版权声明:本文为原创文章,仅代表个人观点,版权归 Frank Zhao 所有,转载时请注明本文出处及文章链接